Medical Device Cybersecurity Vulnerabilities: New FDA Guidance on Informing Patients
The Center for Devices and Radiological Health of the Food and Drug Administration (FDA) has finalized a set of best practices for informing patients and caregivers about cybersecurity vulnerabilities affecting medical devices (Cybersecurity Best Practices). The publication, designed to help industry stakeholders and federal participants “when designing a communication approach for patients and caregivers about cybersecurity vulnerabilities,” is a revised version of a proposal that the FDA released last year to solicit public comments on optimal methods of communicating about such vulnerabilities.1
Cybersecurity vulnerabilities in medical devices obviously can pose extremely serious risks. As devices evolve to be more interconnected, these risks may multiply: vulnerabilities may affect multiple devices using similar software or components. For example, in March of 2020, the FDA communicated a set of 12 vulnerabilities named “SweynTooth”, which impacted a type of wireless communication technology known as Bluetooth Low Energy. These vulnerabilities potentially could be exploited to crash a device, freeze it, or bypass its security. Affected device manufacturers were required to evaluate the risk of the vulnerability to their specific devices, communicate them to patients, and develop remediation actions.
Following the public’s input, in the new Cybersecurity Best Practices, the FDA has refined its guidance on the factors that device industry members and other stakeholders should consider when designing communications about cybersecurity vulnerabilities. These factors include:
- The interpretability of safety communications. To help ensure their effectiveness, communications should be:
- timely, or delivered as early as possible after a reasonable assessment of the nature of the vulnerability, what products were impacted, severity, and mitigating actions;
- relevant, by communicating risks important to the patient;
- readable, clear, and simple, keeping in mind that the target audience may not be familiar with industry terminology or jargon (i.e., “filtering harmful websites” instead of “blacklist”; “data breach” instead of “data leakage”); and
- understandable by linguistically diverse audiences.
- Discussing risks and benefits, including communicating when the probability of cybersecurity exploitation remains unknown, and a consideration of risks associated with mitigation. For example, a communication about an insulin pump’s vulnerability might state:2
- Acknowledging and explaining the unknown, paying specific attention to how this risk is conveyed to avoid omissions or oversight. An example of doing this effectively might be:3

- Availability and findability of information regarding cybersecurity risks, including making the information easy to find in online searches, easy to view on mobile devices, and accessible to individuals with disabilities.
- Guidance on the structure of the communication material, including leading with the most important information first, providing visual cues to draw attention to this important information, and grouping alike information where possible.
- Outreach and distribution vehicles, including giving consideration to the target audience, the key messages, and the means by which to reach the target audience such as via listservs, text messages, social media, television, and/or websites.
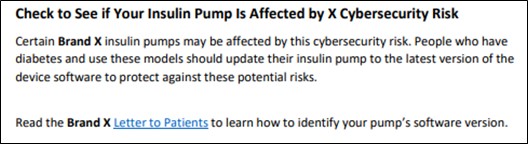
In the appendix to the Cybersecurity Best Practices, the FDA includes a mock-up of a full communication that takes these factors into account:
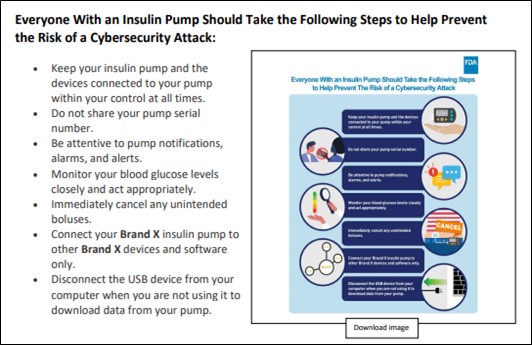
As indicated by these examples, the FDA’s Cybersecurity Best Practices place primary focus on the accessibility of communications to intended recipients, taking into account their likely level of comprehension with respect to complex information. Given the vast differences in educational, linguistic, and other characteristics of members of various patient populations (e.g., age, gender, technological facility, etc.) and the importance of rapid communications of cybersecurity vulnerabilities, industry members will need to consider in advance of discovering a vulnerability how to implement the Best Practices in communicating with affected patients and caregivers. In addition, companies should have communication to patients prior to a vulnerability to explain the risk upfront to patients. These types of communications may affect how FDA and others view the appropriateness of security controls and response.
© Arnold & Porter Kaye Scholer LLP 2021 All Rights Reserved. This Advisory is intended to be a general summary of the law and does not constitute legal advice. You should consult with counsel to determine applicable legal requirements in a specific fact situation.
-
For more information on the FDA’s request for public comments on the Draft Best Practices, please visit Arnold & Porter’s Advisory: “FDA Seeks Comments on Medical Device Cybersecurity Communications Framework Discussion Paper.”
-
Example included in appendix to FDA’s Cybersecurity Best Practices.
-




