DoD Releases Final Cybersecurity Maturity Model Certification Framework and Establishes Cybersecurity Audit and Accreditation Organization
On January 31, 2020, the Department of Defense (DoD) issued its long-awaited final Cybersecurity Maturity Model Certification (CMMC),1 which DoD hopes will combat the immense toll cyber threats have taken on the Defense Industrial Base (DIB), the US economy, and national security.2 The final CMMC provides a comprehensive framework of cybersecurity controls and policies that defense contractors must implement depending on the nature of the information that their information systems will process, store or transmit. In this Advisory, we provide background about the CMMC, describe its structure and principal features, and discuss implementation.
The CMMC and associated DoD guidance suggest that DoD intends to implement the CMMC through procurement-specific solicitation provisions rather than by issuing new Defense Federal Acquisition Regulation Supplement (DFARS) clauses or revising existing DFARS clauses, such as DFARS 252.204-7012, Safeguarding Covered Defense Information and Cyber Incident Reporting. However, as discussed below, the CMMC will materially change what defense contractors must do to safeguard information and will in some respects override aspects of the DFARS 252.204-7012 regime (e.g., eliminating the self-assessment system). As the CMMC is phased in, defense contractors must continue to ensure that they comply with all DFARS 252.204-7012 requirements, which remain relevant for nearly all defense contracts and contractors.
Background
DoD's release of the CMMC is its latest effort to expand cybersecurity requirements to contractors and their supply chains. The modern government cybersecurity system began in earnest in 1988 when Congress enacted the Computer Security Act (CSA), which required the National Bureau of Standards—now the National Institute for Standards and Technology (NIST)—to create guidelines for securing government information systems.3 In 2002, Congress replaced the CSA with the Federal Information Security Modernization Act (amended through the Federal Information Security Modernization Act of 2014 (FISMA)). FISMA requires agencies to, among other things, (1) comply with information security standards developed and implemented in most instances by the Office of Management and Budget (OMB) and NIST and (2) develop information security programs, which must include periodic risk assessments to test vulnerabilities and potential impacts of unauthorized intrusions.4
Although FISMA requires agencies to apply cybersecurity standards to "information systems used or operated by an agency or by a contractor of an agency or other organization on behalf of an agency,"5 there has been substantial uncertainty about how these standards apply to contractors and whether and how contractors must incorporate these security standards into their supply chains. For most federal contractors, the Federal Acquisition Regulation (FAR) contains a limited provision at FAR Subpart 4.19 and contract clause FAR 52.204-21, Basic Safeguarding of Covered Contractor Information Systems,6 which establish baseline security standards for any information system "owned or operated by a contractor that processes, stores, or transmits" "federal contract information" (FCI) (i.e., "information, not intended for public release, that is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government").
DoD contractors, however, have been subject to a broader and evolving set of standards since DoD first implemented cybersecurity standards for the defense supply chain at DFARS 252.204-7012, which has been captioned since 2015 Safeguarding Covered Defense Information and Cyber Incident Reporting. This regulation currently applies to any "unclassified information system that is owned, or operated by or for, a contractor and that processes, stores, or transmits" controlled unclassified information (CUI) that qualifies as "covered defense information" (CDI) under the rule.7Contractors must protect these information systems by, among other things, implementing the security controls in NIST Special Publication (SP) 800-171r1.8 It also directs contractors to report cyber incidents.9 However, this system has lacked verification and enforcement mechanisms, such as independent audits, though the risk of False Claims Act liability looms over potentially noncompliant contractors, as illustrated by the recent United States ex rel. Markus v. Aerojet Rocketdyne Holdings, Inc. case, which Arnold & Porter discussed in a May 2019 article.
CMMC
DoD has determined that more must be done to harden the DIB's and defense supply chain's cyber infrastructure. Enter the CMMC, which DoD announced in May 2019 as a consolidated framework of cybersecurity controls and practices that will apply to contractor-owned and contractor-operated information systems that store or transmit FCI or CUI. The final CMMC follows seven drafts, with the first issued in May 2019 and the seventh issued in December 2019.
CMMC v1.0 incorporates not only the baseline requirements established in FAR 52.204-21 and the cybersecurity controls and practices provided in NIST SP 800-171r1 but also those in Draft NIST SP 800-171B and guidance from other organizations.10 The CMMC also imposes audit and accreditation requirements to provide a mechanism for verifying and enforcing compliance. These requirements will ultimately apply to all contractors and subcontractors throughout the supply chain.11
CMMC Structure
DoD retained the general structure of the draft CMMC versions in the final version. CMMC v1.0 allocates cybersecurity controls and policies through a multi-level system of domains, capabilities, and practices and processes. There are 17 domains, which are categories of cybersecurity controls that build upon the 14 "families" of security controls in NIST SP 800-171:12
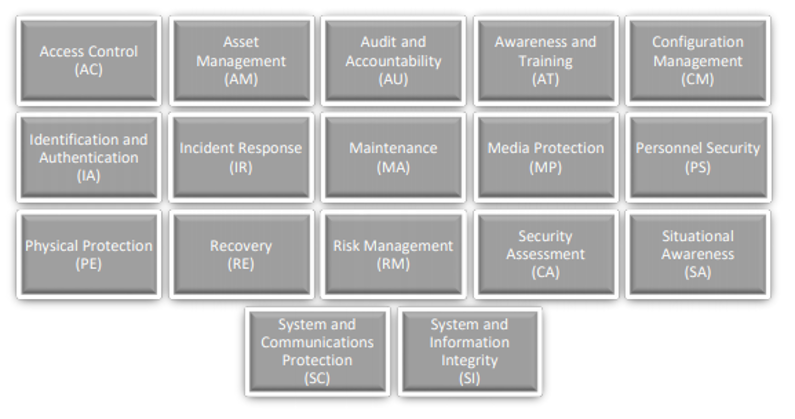
The domains are made of up capabilities.13 These capabilities (i.e., "[a]chievements to ensure cybersecurity within each domain"14) are further divided into specific cybersecurity controls and policies known as practices and processes.15 The practices and processes are allocated across five maturity levels, with Maturity Level 1 imposing baseline security requirements reflected in FAR 52.204-21 and each higher maturity level imposing more intense and sophisticated practices and processes:16
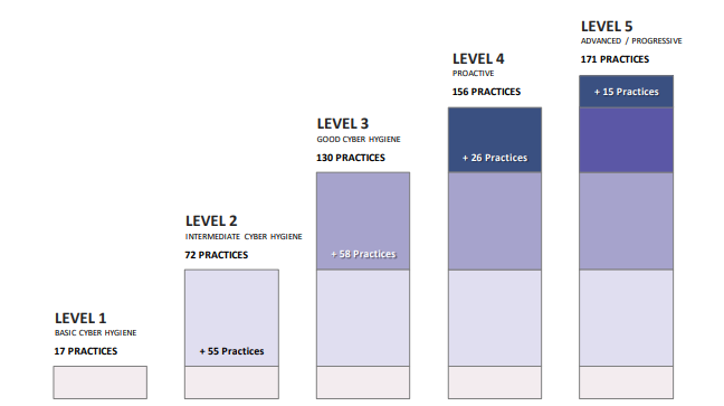
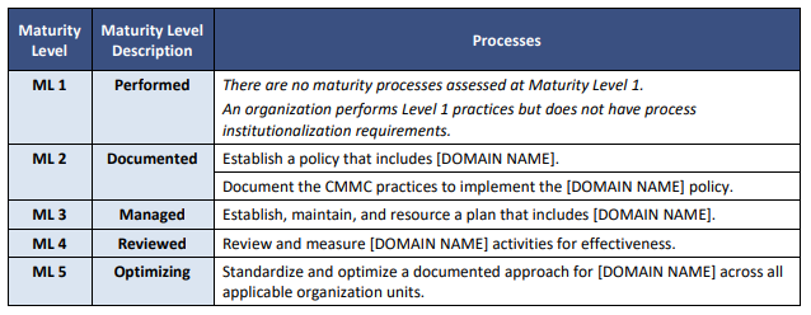
Maturity Level 2 will be a transition step to allow contractors to achieve Maturity Level 3, which organizations must attain to be able to process, store or transmit CUI and which requires organizations to implement security controls in NIST SP 800-171r1.17 Levels 4 and 5 impose more sophisticated requirements, including many controls contained in Draft NIST SP 800-171B.18 Notably, the CMMC tests not only whether specific systems adequately implement the controls in NIST SP 800-171r1 but also the extent to which cybersecurity practices and processes are institutionalized, indicating that DoD expects organizations to secure their cyber infrastructure more broadly, and perhaps even companywide.19
CMMC Implementation and Roll Out
DoD will implement and roll-out the CMMC in phases. These phases include developing assessment and certification procedures and authorities; accrediting assessors; training stakeholders, including industry, on the CMMC; and incorporating the CMMC into DoD contracts.
CMMC Assessment and Certification
DoD recognized that it needed procedures for auditing and certifying CMMC compliance. To accomplish this goal, DoD created a number of stakeholders with defined roles. The most prominent stakeholder is the CMMC Accreditation Body (CMMC-AB), which is a nonprofit, 501(c)(3) organization. According to DoD, which is a CMMC-AB stakeholder, half of the CMMC-AB's directors have small business backgrounds.20 The CMMC-AB's roles and responsibilities will be laid out in a memorandum of understanding (MOU) with DoD that is still in-progress, but the CMMC-AB "will oversee the training, quality and administration of the CMMC third-party assessment organizations" (C-3PAOs) and individual assessors."21
C-3PAOs and individual assessors will be responsible for auditing and certifying companies' compliance with the CMMC.22 These audits will consist of "[i]ndependent review[s] and examination[s] of records and activities to assess the adequacy of system controls, to ensure compliance with established policies and operational procedures, and to recommend necessary changes in controls, policies, or procedures."23 Based on the results of those audits, C-3PAOs and individual assessors will certify an organization as having achieved the maturity level against which it was assessed.24 To ensure independence and avoid conflicts of interest, these assessors will not be allowed to assess their own organizations.25 The CMMC-AB has not yet established procedures for accrediting C-3PAOs and individual assessors, but DoD expects the CMMC-AB to "have a marketplace on their website in March or early April of 2020, where companies can start coming in and getting information."26
CMMC Training
DoD is working with the Defense Acquisition University (DAU) to develop CMMC training.27 This training should be posted to DAU's website in or around June 2020.28
CMMC Implementation
DoD expects to begin implementing the CMMC and applying those requirements to contractors and their supply chains in or around March 2020. This process will begin with a "pathfinder" program. Although DoD believes it has a strong understanding of how burdensome the CMMC will be when implementing the CMMC, DoD will use pathfinders to test the CMMC process and determine "how long it is actually taking for someone to come in who's never seen the model actually run through an assessment."29
Contractors can expect DoD to begin incorporating the CMMC into requests for information (RFIs) beginning in June 2020 with contract awards incorporating the CMMC starting in Fiscal Year (FY) 2021.30 The CMMC will initially be limited to "candidate programs."31 It is not clear how many procurements this initial implementation will affect, but reports suggest that roughly 10 to 20 procurements may be impacted in the short-term.32 DoD will ultimately incorporate the CMMC into every new DoD contract—including other transaction agreements (OTAs)—starting in FY 2026.33
Key Takeaways
The CMMC is a groundbreaking new cybersecurity effort that will have vast implications for contractors as DoD implements it over the next six years and as it becomes mandatory for all DoD contractors and their supply chains. As of June 2019, only one percent of the DIB had implemented NIST SP 800-171's 100 security controls.34 The implementation of CMMC will likely increase this number dramatically. Moving forward, contractors should bear in mind the following takeaways:
- Although the CMMC may not formally impact many contracts in the short-term, contractors would be wise to begin familiarizing themselves with the CMMC and working to implement its requirements, starting with developing a plan of action and milestones (POAM) and system security plan (SSP). Companies that implement the CMMC will be well positioned to compete for future DoD contracts incorporating these obligations—with solicitations being released as early as the latter part of 2020—and requiring authorizations to operate (ATOs) while those that do not incorporate the CMMC will find themselves ineligible for award.
- Costs associated with becoming CMMC certified are "allowable, reimbursable cost[s]."35 Contractors can expect to be able to allocate CMMC certification costs indirectly across their DoD contracts, but the extent of the costs covered remains to be seen. Costs associated with the actual certification process (i.e., costs incurred from the time a contractor requests that a CMMC-AB-accredited assessor certify that the contractor has implemented relevant CMMC practices and processes) will likely be allowable and thus reimbursable. However, it is not clear whether costs of becoming CMMC compliant (i.e., the costs associated with implementing relevant CMMC practices and processes) will be considered allowable.
- The CMMC will introduce new litigation risks. In the procurement process, contractors should expect cybersecurity to play a larger role in DoD procurements, including best-value determinations,36 and can expect bid protests implicating cybersecurity concerns to increase for DoD procurements. Defense contractors that fail to satisfy applicable CMMC requirements or to maintain their systems to remain in compliance could face contract claims under the Contract Disputes Act and False Claims Act liability.
- The CMMC will have extensive impacts on contractors' supply chains. Defense contractors will need to ensure that they incorporate the CMMC requirements into their subcontracts and verify that their subcontractors have in fact complied with the CMMC and received the requisite certifications.
- Although the CMMC establishes a consolidated framework of security controls, defense contractors will remain subject to existing compliance obligations. For example, the CMMC does not obviate the safeguarding or cyber incident reporting requirements established in DFARS 252.204-7012. Rather, the CMMC establishes a mechanism for demonstrating compliance with the safeguarding provisions of the rule, which remain in effect and builds upon those requirements.
-
CMMC Model v1.0 Briefing; CMMC Model v1.0; CMMC Model v1.0 Appendices. Arnold & Porter previously discussed the draft CMMC version 0.4 in September 2019.
-
DoD noted that "{t}he Council of Economic Advisors estimates that malicious cyber activity cost the U.S. economy between $57 billion and $109 billion in 2016." CMMC Model v1.0, supra n.1, at 1.
-
Computer Security Act of 1987, Pub. L. No. 100-235 (Jan. 8, 1988).
-
-
-
81 Fed. Reg. 30439 (May 16, 2016).
-
DFARS 252.204-7012(a). CUI is any unclassified information subject to "safeguarding or dissemination controls." 32 C.F.R. § 2002.4(h). Categories and subcategories of CUI are identified in the CUI Registry. CDI is CUI that "is (1) Marked or otherwise identified in the contract, task order, or delivery order and provided to the contractor by or on behalf of DoD in support of the performance of the contract; or (2) Collected, developed, received, transmitted, used, or stored by or on behalf of the contractor in support of the performance of the contract." DFARS 252.204-7012(a).
-
-
-
CMMC Frequently Asked Questions (FAQs), at Question 8, (last visited Feb. 6, 2020).
-
Id. at Question 21 ("{A}ll companies doing business with the Department of Defense will need to obtain CMMC.").
-
Compare CMMC Model v1.0, supra n.1, at 7 with NIST SP 800-17r1 at 7. As indicated in Arnold & Porter's prior CMMC article discussing CMMC Draft Version 0.4, DoD proposed 18 categories. Through the drafting process, DoD removed the Cybersecurity Governance domain. Compare CMMC Draft Version 0.4 Release & Request for Feedback at 10 with CMMC Draft Version 0.6 Preface at 5 and CMMC Model v1.0, supra n.1, at 7.
-
CMMC Model v1.0, supra n.1, at 8.
-
CMMC Draft v0.4 Overview at 8.
-
CMMC Model v1.0, supra n.1, at 7-8.
-
-
-
-
-
Press Briefing by Under Secretary of Defense for Acquisition & Sustainment Ellen M. Lord, Assistant Secretary of Defense for Acquisition Kevin Fahey, and Chief Information Security Officer for Acquisition Katie Arrington, DoD (Jan. 31, 2020), (hereinafter "DoD Press Briefing").
-
-
DoD has suggested that assessments for the highest maturity levels "may be performed by organic DoD assessors within the Services, the Defense Contract Management Agency (DCMA) or the Defense Counterintelligence and Security Agency (DCSA)." CMMC FAQs, supra n.11, at Question 14.
-
CMMC-AB Glossary, (last visited Feb. 6, 2020).
-
DoD Press Briefing, supra n.21.
-
-
DoD Press Briefing, supra n.21.
-
-
-
Lauren C. Williams, A sneak peek at CMMC, FCW (Jan. 29, 2020).
-
DoD Press Briefing, supra n.21.
-
-
Jared Serbu, Pentagon issues long-awaited cyber framework for Defense Industry, Fed. News. Network (Jan. 31, 2020), (indicating the initial roll-out will be limited to 10 contracts); Travis J. Tritten, Defense Contractor Cybersecurity Audits Move Closer to Reality, Bloomberg Gov't (Jan. 31, 2020), (indicating the initial roll-out will apply to 20 procurements).
-
DoD Press Briefing, supra n.21.
-
Jason Miller, Why DoD's Decision to make cybersecurity an 'allowable cost' matters, Federal News Network (June 17, 2019).
-
CMMC FAQs, supra n.11, at Question 19.
-
Catherine R. Tucciarello, et al., "Help Me, Help You": Defense Department Advises Contractors That Cybersecurity Is An Allowable Cost, Nat'l L. Rev. (June 24, 2019), ("'We cannot look at security and be willing to trade off to get lower cost, better performing product or to get something faster. If we do that, nothing works and it will cost me more in the long run.'" (quoting Katie Arrington, DoD's Chief Information Security Officer for the Assistant Secretary for Defense Acquisition)).






